The smart Trick of Risk Management Enterprise That Nobody is Talking About
Wiki Article
Get This Report on Risk Management Enterprise
Table of ContentsRisk Management Enterprise - An OverviewSome Known Incorrect Statements About Risk Management Enterprise Unknown Facts About Risk Management EnterpriseRisk Management Enterprise Fundamentals ExplainedRisk Management Enterprise for BeginnersSome Known Factual Statements About Risk Management Enterprise Risk Management Enterprise Fundamentals Explained
Here are several of its essential features that facilities have to recognize. So, take a look. Real-Time Risk Analyses and Mitigation in this software allow companies to constantly keep an eye on and evaluate dangers as they progress. This function leverages real-time information and automatic evaluation to identify potential risks immediately. As soon as risks are identified, the software program facilitates prompt mitigation activities.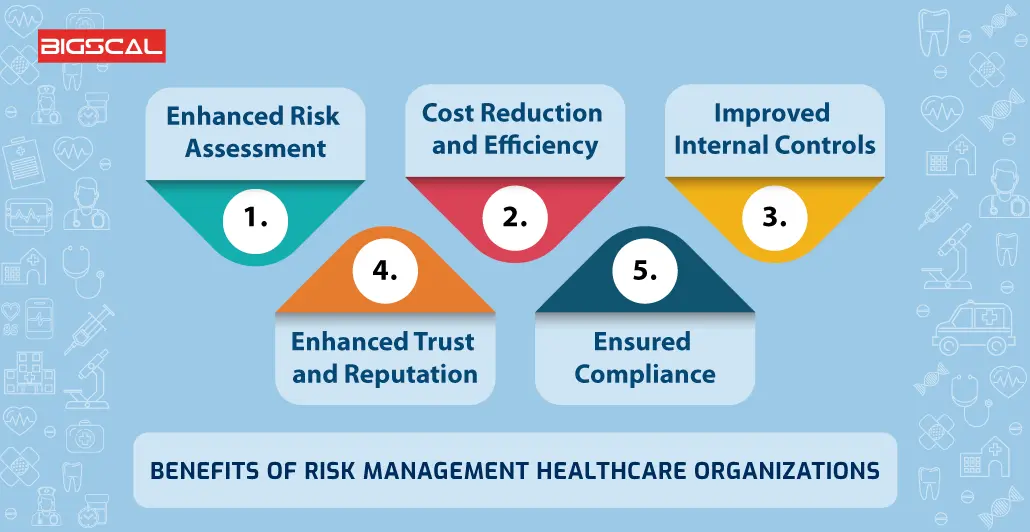
KRIs solve the problem of irregular or uncertain risk assessment. They deal with the challenge of recurring risk monitoring by offering tools to keep an eye on threats continuously. KRIs enhance safety danger oversight, making sure that prospective risks are identified and taken care of successfully. The job of threat administration must not be an obstacle. Organizations have to count on a top-notch and sophisticated threat management software.
The Best Guide To Risk Management Enterprise
IT risk administration is a subset of business danger administration (ERM), made to bring IT take the chance of according to an organization's threat hunger. IT run the risk of management (ITRM) includes the plans, procedures and technology essential to reduce dangers and susceptabilities, while preserving compliance with appropriate regulative requirements. In enhancement, ITRM seeks to restrict the repercussions of destructive events, such as safety breaches.While ITRM structures offer valuable advice, it's easy for IT groups to struggle with "structure overload." Veronica Rose, ISACA board supervisor and a details systems auditor at Metropol Corp. Ltd., recommends the use of a combination of structures to achieve the most effective outcomes. The ISACA Threat IT framework aligns well with the COBIT 2019 structure, Rose claimed.
Venture Threat Monitoring Software Application Growth: Conveniences & Qualities, Price. With technological developments, threats are continually on the rise., services browse via a constantly altering sea of dangers.
Some Known Incorrect Statements About Risk Management Enterprise
In this blog site, we will study the world of ERM software application, discovering what it is, its benefits, attributes, and so on to make sure that you can construct one for your company. Business Danger Management (ERM) software is the application program for preparation, guiding, arranging, and regulating business tasks and simplifying risk management processes.With ERM, companies can make informative choices to improve the total strength of business. Read: ERP Application Growth Devoted ERM systems are critical for organizations that regularly deal with large quantities of delicate details and several stakeholders to authorize critical choices. Some industries where ERM has come to be a standard system are health care, financing, construction, insurance, and infotech (IT).
: It is difficult for any type of business to undertake an extensive audit. It can be stayed clear of by using the ERM software system. This system automates law conformity administration to keep the organization secure and compliant. Apart from that, it likewise logs and categorizes all the documents in the system making it much easier for auditors to review processes a lot quicker.
How Risk Management Enterprise can Save You Time, Stress, and Money.
You can likewise link existing software application systems to the ERM via APIs or by adding data by hand. Businesses can utilize ERM to assess dangers based on their prospective effect for better threat management and mitigation.: Adding this attribute enables individuals to obtain real-time notifications on their gadgets concerning any type of danger that could take place and more info its effect.
Rather, the software application allows them to establish thresholds for various processes and send push notices in instance of possible threats.: By incorporating data visualization and reporting in the personalized ERM software program, businesses can acquire clear insights concerning threat fads and performance.: It is mandatory for companies to abide by sector conformity and regulatory requirements.
These systems enable companies to carry out best-practice danger monitoring procedures that align with industry standards, offering a powerful, technology-driven method to identifying, evaluating, and mitigating risks. This blog site checks out the benefits of automatic danger management tools, the locations of threat monitoring they can automate, and the value they give a company.
Things about Risk Management Enterprise
Groups can establish kinds with the pertinent areas and quickly produce various forms for different threat types. These threat evaluation kinds can be circulated for completion through automated workflows that send alerts to the appropriate personnel to complete the forms online. If forms are not completed by the deadline, after that chaser e-mails are automatically sent by the system.The control monitoring and control screening process can also be automated. Firms can make use of computerized workflows to send out routine control examination notices and team can go into the results through online types. Controls can additionally be kept track of by the software application by establishing rules to send notifies based on control information kept in various other systems and spread sheets that is pulled into the system by means of API combinations.
Threat administration automation software program can also sustain with danger reporting for all levels of the venture. Leaders can watch reports on threat direct exposure and control efficiency through a variety of reporting outcomes including static records, Power BI interactive records, bowtie analysis, and Monte Carlo simulations. The capability to draw genuine time records at the touch of a switch reduces out tough information adjustment jobs leaving threat teams with even more time to analyze the data and encourage business on the most effective strategy.
Organizations operating in affordable, fast-changing markets can't pay for delays or inefficiencies in attending to prospective threats. Typical threat management making use of hands-on spreadsheet-based procedures, while familiar, often lead to fragmented information, time-consuming coverage, and a boosted chance of human error.
Not known Facts About Risk Management Enterprise
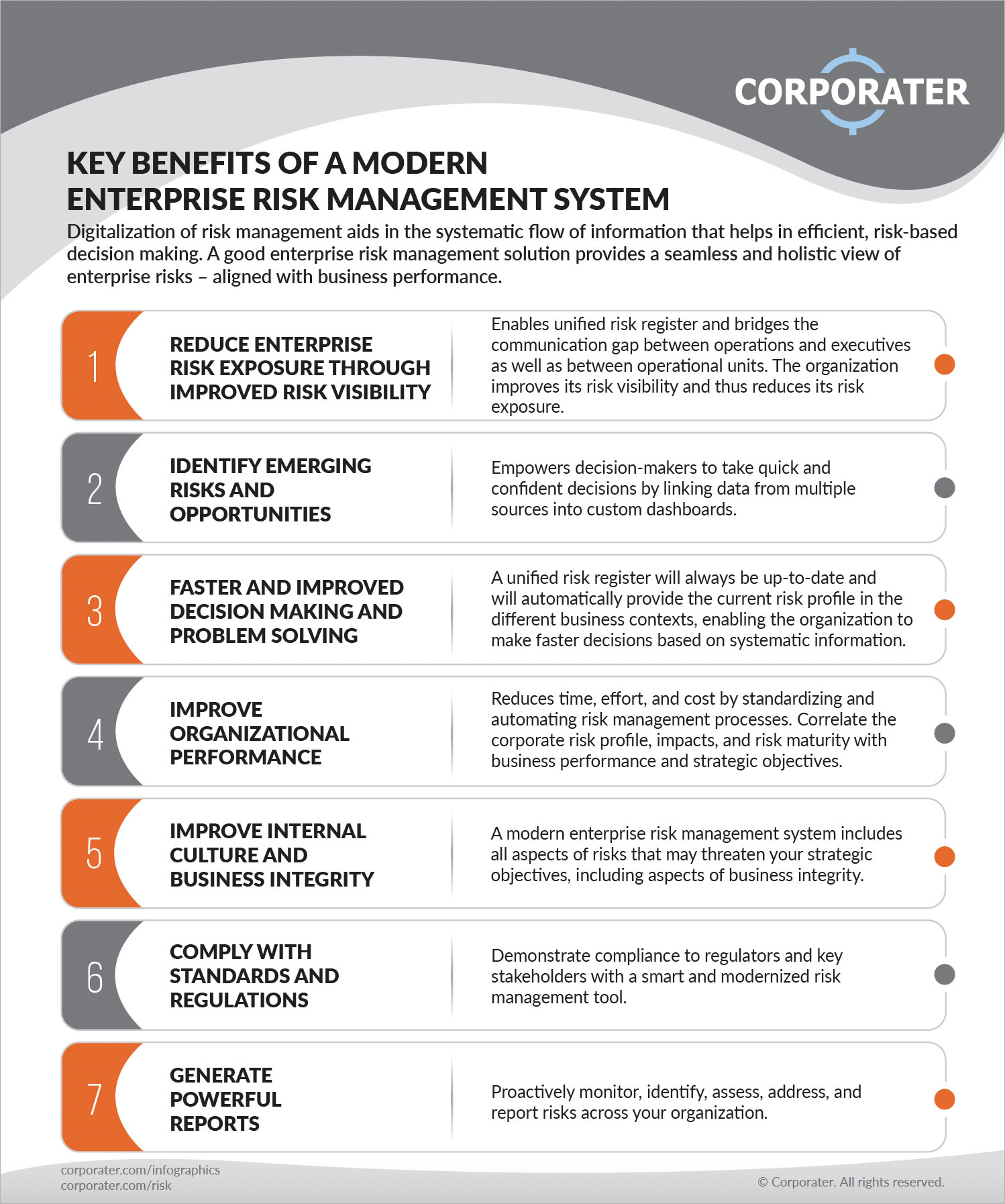
This ensures danger signs up are constantly present and aligned with organizational goals. Compliance is an additional vital chauffeur for automating danger administration. Specifications like ISO 31000, CPS 230 and COSO all offer advice around danger monitoring finest techniques and control structures, and automated threat administration tools are structured to line up with these demands helping firms to satisfy most commonly utilized danger monitoring requirements.Search for risk software application systems with a consents hierarchy to easily set up workflows for risk escalation. This performance allows you to customize the view for every user, so they just see the data relevant to them. Make sure the ERM software program offers user tracking so you can see who entered what information and when.
Choose a cloud-based platform to ensure the system receives regular updates from the supplier including brand-new capability. Look for devices that use job threat administration capacities to manage your tasks and portfolios and the connected risks. The benefits of taking on threat monitoring automation software expand far past effectiveness. Organizations that incorporate these solutions right into their ERM approach can expect a host of substantial and abstract.
Rumored Buzz on Risk Management Enterprise
While the case for automation is compelling, applying a threat administration platform is not without its obstacles. To get rid of the obstacles of threat monitoring automation, companies need to spend in information cleaning and administration to ensure a solid foundation for executing an automated system.Automation in threat administration equips organizations to change their method to risk and construct a stronger foundation for the future (Risk Management Enterprise). The question is no more whether to automate threat monitoring, it's how quickly you can begin. To see the Riskonnect at work,
The answer typically exists in exactly how well threats are expected and managed. Task management software program offers as the navigator in the tumultuous waters of project execution, offering devices that determine and assess threats and devise methods to minimize them efficiently.
Report this wiki page